Device Administration Overview
In this section of the course, we’ll be looking at how we can utilise Cisco ISE to manage Device Administration. In this lesson, we’ll be looking at what we can use the service for and how we can configure it on our Cisco ISE server.
Overview
Let’s start with the basics… what is device administration?
Device administration is a service provided by the Cisco ISE platform used to control and audit our network devices.
In essence, our network devices will be configured to query our Cisco ISE server for the following purposes:
This is achieved using AAA services:
INSERT EXAMPLE
In order to provide some context, let’s take a look at our example above.
Here you can see we’ve pointed our multiple network devices to Cisco ISE. This then provides us a number of benefits:
In our example company, we have two teams; Helpdesk and Operations. With the device administration feature, we have the ability to provide tiered access depending upon job roles.
We might provide our Helpdesk read-only access to all network devices. We might then provide our Operations team full administration access.
The device administration feature works by utilising a protocol known as TACACS+. We’ll learn more about this in our upcoming lesson here.
Licensing
In order to use the device administration feature, the licensing is extremely straight forward. The only license that’s required is the Device Admin license.
Unlike other licenses within the Cisco ISE suite, the device admin license is perpetual. Once purchased, you can utilise the feature forever.
Within high-availability Cisco ISE deployments, you might have a number of nodes authenticating TACACS+ requests.
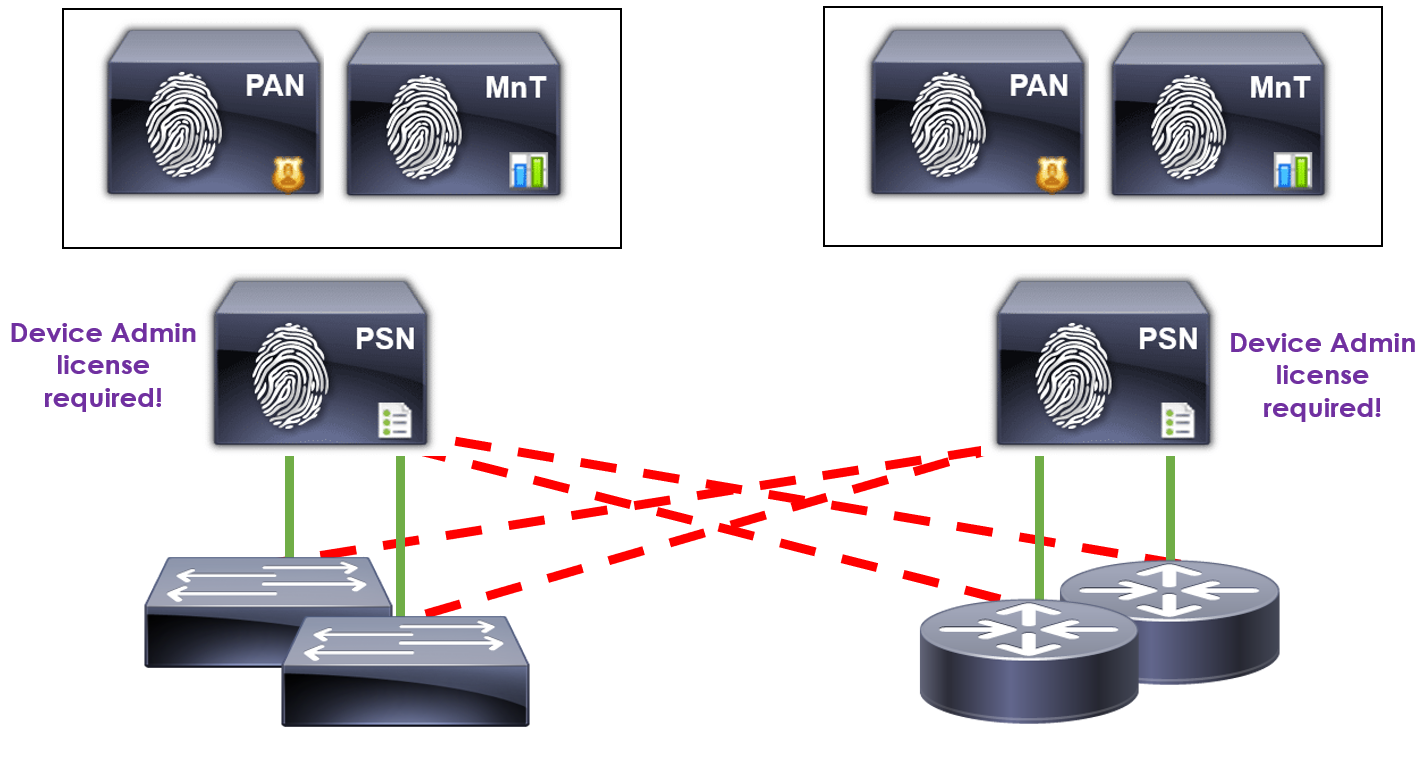
In our example, we have two Policy Service Nodes (PSN) authenticating TACACS+ requests. As such, each node authenticating TACACS+ requests requires a device admin license.
For our topology, we’ll require two device admin licenses. One for MN-PSN01 and other for MN-PSN02.
Configuration
The device administration requires a number of steps to be configured in order to operate. This includes configuration on both Cisco ISE and our network devices.
Over the upcoming lessons, we’ll look at the configuration required on Cisco ISE and a number of common network devices.
Cisco ISE Configuration Steps:
Network Device Configuration: